It's no longer a secret: it's now easy for anyone who can afford it to afford a machine for a few thousand euros capable of accessing the content of any iPhone. To do this, there are two solutions: go through the darknet, or take advantage of the privilege granted to institutions using this type of device - officially - under the cover of national security.
The reality is more vague, so much so that it is difficult to know the real list of Cellebrite orGrayshift, two companies designing these machines. Even more so when a precise manual for using them arrives in the hands ofVice, whose particularly mainstream audience goes beyond the boundaries of Apple consumers. In recent years, under the leadership of Tim Cook, the latter has nevertheless made a point of praising the confidentiality promises of its products.
© Vice / Motherboard
A technique well known to experts
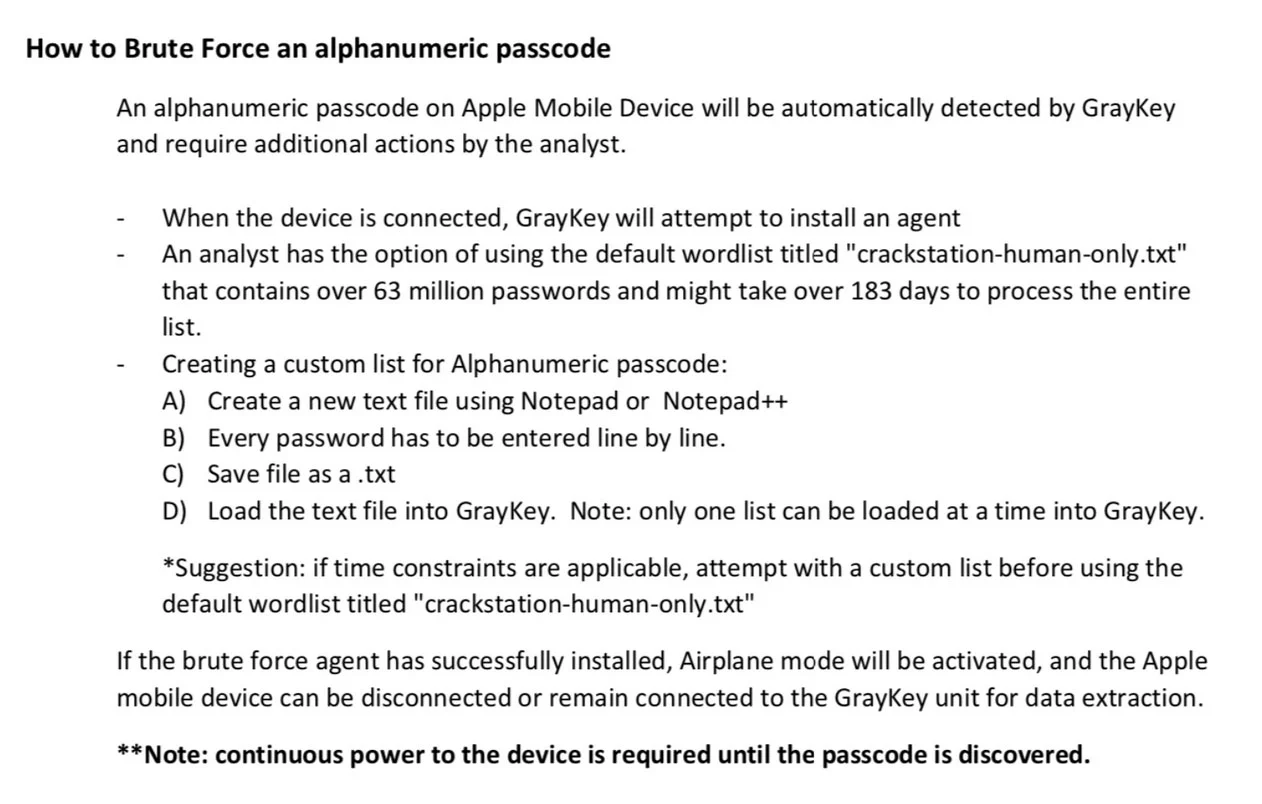
The method favored by GrayKey (this is the name of the device) to attack an iPhone is in reality nothing other thanbrute force. Strategy well known to players in the sector, sincewe also find it at the heart of the San Bernardino affair. At the time, it was the FBI which bet on another company also specializing in hacking.
Obviously, all this is not very convenient for Apple, which therefore faces a lot of criticism relating to the protection supposed to be offered by its smartphones. The firm is also playing cat and mouse with these intruders, who are also at the origin of discoveries of major flaws then filled by Cupertino.

© Vice / Motherboard
Almost no barriers
As shown in the screenshots obtained byMotherboard, GrayKey is able to unlock an iPhone almost unconditionally. In fact, the software even knows how to access iOS content when the device is turned off or only has a small percentage of battery life left. To go faster, a feature called HideUI also makes it possible to identify the user's password (like a keylogger) by recording their keystrokes.
Even with the best will in the world, it is not tomorrow that there will be an inviolable operating system. But thebug bountiesare also there to advance existing technologies, so Apple is also counting on these rewards to reverse the balance.
© Vice / Motherboard

i-nfo.fr - Official iPhon.fr app
By : Keleops AG